In the past two lessons, you’ve learned about choosing the right antivirus for your computer and enhancing your security with next-generation anti-hacking tools.
But to understand how they protect you and why it’s necessary to be mindful of your own actions on the Internet, we need to answer an essential question:
What are the dangers that threaten your data’s security?
If you’re like me, you surely have a bunch of gadgets you use constantly. And they’re probably connected to the Internet as well (otherwise they’d be pretty much useless).
How many of the devices in this list do you own?
- Computer (laptop/desktop)
- Smartphone
- Tablet
- TV
- Kindle
- Photo camera
- Printer/scanner
- MP3 player
- Gaming console
- GPS
- DVD player
- Sports bracelet
- Headphones.
Naturally, the list could go on and on, but the key takeaway here is that at least 7 or 8 of this list of gadgets can be Internet-connected, and, consequently, hackable.
Globally, there will be 27.1 billion networked devices in 2021. These connected devices outnumber people by three to one.
So let’s get down to the nuts & bolts:
Say you have a computer, a smartphone, a tablet and a TV that are connected to the Internet through your home’s Wi-fi connection.
They will be vulnerable in a number of ways against cyber criminals and their intentions:
- Your home Wi-fi network can be easily hacked if you don’t take the necessary precautions (a dedicated guide is coming in lesson #12).
- Your computer can be compromised in a number of ways, both through software (malware, viruses, Trojans, etc.) and through hardware (infected USBs, for example).
- Your smartphone could fall prey to malvertising when browsing the web via a public Wi-Fi hotspot without adequate protection.
- Your tablet can be compromised through malware by installing a rogue app or by visiting an infected website.
- Even smart TVs are vulnerable to hacking attempts, although they’re not as susceptible as other gadgets. But they may be invading your privacy, by collecting your browsing data and other confidential information gathered through their voice recognition technology.
All these vulnerabilities (and many, many more) come from a variety of sources, and cyber criminals know how to exploit them.
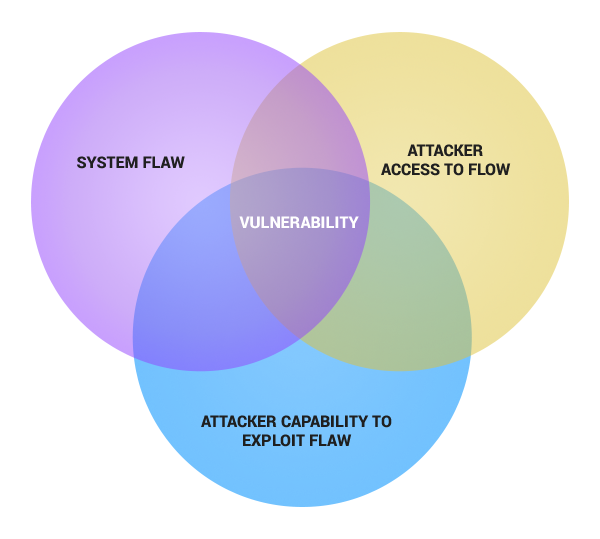
But what is a vulnerability?
A cyber security vulnerability is a weakness which allows an attacker to undermine a system’s data security defenses. It’s the Achilles heel of your computer.
A vulnerability appears at the intersection of 3 elements:
- The software itself has a coding flaw (example: the software can automatically download a type of file from the internet)
- The attacker can activate the flaw (example: you click on a malware-infected banner ad which delivers a download on your computer)
- The attacker can now exploit the flaw (example: now the cyber criminal has a way in, through that malicious download).
Between 60% and 90% of cyberattacks are caused by a security hole in the software you use, which makes it the most used attack vector hackers employ.
So what should you watch out for?
Here are the most vulnerable 3rd party software on the market:
- Oracle Java Runtime environment
- Adobe Acrobat Reader
- Adobe Flash Player / Plugin
- Apple Quicktime
The bad news is that you’re probably using at least 3 of these types of software right now!
The good news is that you can do something about it!
Here’s how you can manage your vulnerabilities:
- Never ignore an update prompt again! Make sure you install updates as soon as they’re available or use an automatic patching software that delivers updates silently and without interrupting your work. Heimdal Premium Security Home is such an option that you can install in under 2 minutes and which won’t impact your computer’s performance.
- If you don’t use it constantly, uninstall it. Software on your computer that you rarely use most likely hasn’t been updated in a long while, so it can become a security risk. Protect yourself and uninstall it.
- Don’t feed your computer junk. The key to keeping your computer safe and performing well is to not install bad software. Unless it comes from a software maker you trust, you shouldn’t install it. The same goes for browser add-ons.
- Use a good antivirus. Although it doesn’t offer complete protection, antivirus is essential for your system’s security. Run an in depth scan once in a while – it will do you a world of good.
- Use next-generation anti-hacking tools. Your antivirus is a reactive solution, but you need a proactive one as well. Heimdal Premium Security Home comes with built in traffic-scanning and strong anti-malware capabilities. This works proactively and strengthens your defenses substantially.
- Keep an eye out for trouble. Make sure to monitor any suspicious behavior on your computer. In lesson #17 you’ll learn all about detecting cyberattacks and mitigating their consequences, so stay tuned.
Vulnerability management is something every Internet user should do, not just companies.
That’s it for now, but let’s see what’s coming up in the next lesson (#9):
Do you keep postponing that data back-up, because you don’t really think it’s necessary?
This course is presented in partnership with Heimdal Security – a worldwide leader in enterprise and consumer cyber security solutions.



