Encryption tools are very useful in keeping valuable information hidden from cyber criminals, because it renders the data inaccessible to prying eyes.
But what exactly is data encryption?
Encryption is a process that transforms accessible data or information into an unintelligible code that cannot be read or understood by normal means.
The encryption process uses a key and an algorithm to turn the accessible data into an encoded piece of information.
To decode the encrypted data and render it back to its original form (that can be easily understood), one needs access to the ciphering algorithm and the secret key that was used.
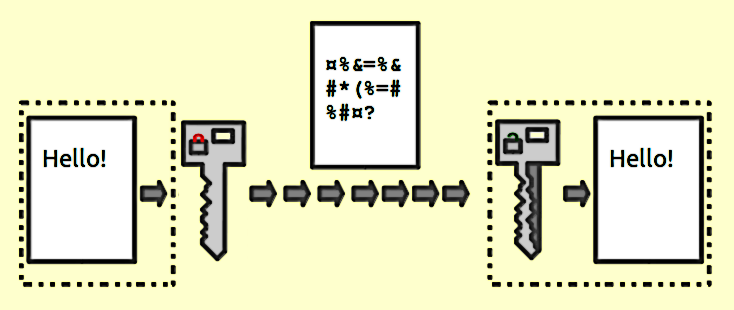
The purpose of encryption is to secure sensitive information from cyber criminals or other online threats. At the same time, it’s a method that can be used to archive large amounts of data or to secure private communication over the Internet.
So while security analysts around the globe try to find the best solutions to ensure privacy, let’s focus on how you can encrypt your files without losing speed of access and usability.
Use strong passwords for your online accounts
We could jump directly to the best ways to encrypt your files, but encrypting files isn’t that helpful if it’s based on a weak password.
When setting up your encryption process, you’ll be asked to choose a password that will act like the decryption key. So your encryption is only as good as your password.
That’s why you need to make sure we use strong passwords, which contain different character types, like uppercase and lowercase letters and numbers, and are more than 15 characters long.
There are even several ways you can test if your passwords are strong enough.
Also, you’ll need to set passwords which are not easy to remember or guess, and which aren’t used for more than one online account.
It may sound like a hassle and you’re probably asking yourself:
But how exactly am I supposed to do this, when I have so many online accounts?
For most users, the “solution” is to simply use the same credentials. But this an incredibly poor choice.
As we mentioned, if a malicious hacker discovers the password you use for one online account, he’ll easily be able to use the same credentials to access all the other accounts where you reused that password. So NEVER, EVER reuse your passwords!
1. LastPass
To protect your passwords and increase your online safety, we recommend a password manager like LastPass. Using a password manager means you’ll only need to remember one password, the one you use to access LastPass.
LastPass provides extensions for the main web browsers, like Mozilla Firefox and Google Chrome, so it’s easy to use.
When you create a new online account, it immediately provides the option to save the new credentials.
This password managers (and others like it) also encourages you to set an unique and hard to break password and discourages password reuse. If you’re using the same password for multiple accounts, it simply recommends selecting a different password.
Managing passwords safely can really become much easier if you use two-factor authentication whenever it’s available.
Encrypt Your Hard Drive
1. BitLocker
There is a large number of encryption tools available out there, which can be used to encrypt data locally. For most users, the easiest way to encrypt sensitive information or maybe the entire hard-disk is to use Microsoft’s BitLocker software, which is installed on most Windows operating systems.
What exactly is BitLocker?
BitLocker is a full-disk encryption tool incorporated in the latest Windows operating systems, which supports AES (128 and 256-bit) encryption (military grade).
What is AES encryption used by most security software?
The Advanced Encryption Standard has been tested and improved and is now used worldwide by most security vendors due to its high level of security and optimization.
Why we recommend you use BitLocker
It’s easy to use and it’s already integrated into your Windows operating system.
BitLocker Drive Encryption is mainly a tool you can use to prevent data breaches and data ex-filtration from your hard disk. That’s because BitLocker encrypts the entire drive, which makes it impossible for anyone stealing your laptop to remove the hard drive and read the files. It’s a also a good safeguard if you should lose your PC.
It’s also good to know that, if you have BitLocker Drive Encryption activated, when you add new files, BitLocker will encrypt them automatically.
Encrypt Your Files
1. 7Zip
There are many users that don’t want to encrypt the entire hard disk, but only specific files and documents that include valuable data or information. This is especially the case for stuff you need to send over the Internet.
7Zip is a powerful and lightweight solution whose main asset is simplicity. As many users noticed, 7Zip is capable of extracting most archives and it features strong AES-256 encryption.
The program is easy to get used to when encrypting your own files and it uses one of the best compression formats. It’s also available in 87 languages and compatible with even the oldest of Windows versions, plus Linux.
2. AxCrypt
Like 7Zip, AxCrypt is a lightweight free encryption tool that integrates with Windows. You can use it mainly for protecting valuable files from the system.
The files can be encrypted for a specific period of time and can auto-decrypt later on, when that file reaches the destination. It’s a fast tool that enables you to select an entire folder or a group of files and encrypt them fast.
As I mentioned at the beginning, its main purpose is to protect specific files and not entire hard drives, although it does offer protection against major cracking methods used by cyber criminals. Plus, you can use it to encrypt your sensitive data before backing it up in the cloud or on external hard drives.
Encrypt your Online Traffic
Encryption for private files is not enough. To increase your overall protection, you need to make sure no one can eavesdrop on your communication over the web.
So, how can I increase my online security without creating too many barriers that may slow down my access to information posted online?
I have listed below a few simple tools you can use to access online content and stay safe from privacy breaches at the same time. Two birds, one stone.
1. Access secure websites that use encryption mechanisms
To make sure you always access secure web pages, you can use a browser extension like HTTPS Everywhere, which works on Mozilla Firefox, Opera and Google Chrome.
Though some security analysts argue that even secure websites aren’t bulletproof, it’s much better than doing nothing. After all, these secure websites use some encryption and authentication standards that are meant to ensure the confidentiality of your online activities.
When you use HTTPS Everywhere, your browser will go through an authentication process while connecting to a secure website. This process uses cryptography to verify that a secure connection is maintained.
Using a little extension like HTTPS Everywhere, which encrypts your communication with major websites, will make your online activities more secure from the dangers of cybercrime.
7. Tor Browser – Access the Anonymity Network
What If I want even more protection and online privacy?
If you want something close to complete privacy, you can use the Tor browser. This allows you to access Internet anonymously using the Tor network of computers.
The special Tor Browser has been designed to be used by anyone who wants to conceal any browsing activity from prying eyes.
What exactly is Tor?
Tor is the short version of “The Onion Router” and it is the browser you just read about, but also stands for the anonymity network. Here’s a useful summary from Wikipedia:
Tor directs Internet traffic through a free, worldwide, volunteer network consisting of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult for Internet activity to be traced back to the user: this includes “visits to Web sites, online posts, instant messages, and other communication forms”. Tor’s use is intended to protect the personal privacy of users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored.
The number of computers in the network become a highly effective layer of protection that conceals the user identity.
Elements of insecurity
You may have heard already about cases where Tor anonymity network has been used for malicious purposes (especially in ransomware attacks).
And there are a high number of articles which show how this anonymity network is being used by online criminals to hide their communication from law enforcement agencies or to promote their exploit kits-as-a-service business.
We understand you may see some connections between your online browsing and criminal activities, but as Tor network representatives mention, they simply want to provide the same privacy privileges that cyber criminals already access.
8. Virtual Private Network – Encrypt Your Communication
Are there more alternatives for becoming anonymous online?
YES!
To connect in complete privacy to any online location in the world, you can use a VPN, which is a Virtual Private Network.
This private network is able to spread across the normal Internet space, using its resources to create an encrypted channel that can keep your communication safe from interception attempts.
Usually, employees who work remotely use a VPN to access the private company network. This way, they can run online operations or transfer highly confidential documents in complete privacy.
But that doesn’t mean VPN software is just for corporate users. I recommend you use this type of software when connecting to unsafe public networks or when you want to access content whose distribution is restricted to a certain geographical area.
Therefore, if you choose to use VPN software, you can ensure that your web traffic and valuable information remain encrypted. Cyber criminals won’t be able to sniff the data you exchange online and collect sensitive info such as passwords and usernames, credit card details and more.
To keep your online session private over the Internet and be safe from cyber attacks, use a popular VPN solution like CyberGhost.
9. Online Proxy Server – Hide Your IP Address
If you don’t want to go through the process of finding and installing a VPN or the Tor browser, you can still rely on a basic privacy measure: an online proxy server.
Using a proxy server, you can simply hide your IP address and surf online accessing websites anonymously.
Keep in mind that a web proxy server can’t offer the encryption channel you get from a VPN solution and can’t hide your online communication through an entire network like Tor. But you’ll still have an indirect link between your computer and the website you access. This should provide baseline protection for small browsing activities.
If you’re a Windows 10 user and want to see how you can set up a proxy, these instructions can come in handy.
Encryption is not enough
To keep your valuable information safe from cyber criminals, encryption is not enough. In our blogposts, we often emphasize that no single security solution is enough.
The cyber criminals’ arsenal includes a lot of weapons that we need to shield our systems from. Since there are so many dangers online, there are a few more things you can do to improve your onlinse security:
- Keep your browser and operating system updated with the latest security patches. Make sure you have the latest versions running on your system. Online criminals spread malicious tools by using security exploits to take advantage from your system’s vulnerabilities. Patching is key, as the experts said it again and again.
- Use a reliable security solution from a trusted company. To keep your system safe from the latest threats, the software should include a real-time traffic scanning engine. This ensures that every connection to and from the Internet is scanned for threats. Start with an antivirus, but don’t forget that it, too, is not enough.
- Be careful when connecting to public and free wireless networks. One of the favorite methods used by online criminals to retrieve your credentials is to use wireless sniffers to access data you send over unprotected networks.
Conclusion
As you might have guessed, encryption is a pretty solid last line of defense against a malicious attack. Even if they somehow manage to pierce through your other security layers such as antivirus or two factor authentication, they might still not be able to get a hold of your data, because encryption lockdown.
This course is presented in partnership with Heimdal Security – a worldwide leader in enterprise and consumer cyber security solutions.



