Password Hygiene
Have you ever used the same password for more than one of your accounts?
The answer is probably YES and that’s a BIG PROBLEM.
This lesson is a staple in your education about cyber security.
The lead character is that string of characters that shield our most prized information:
The mighty PASSWORD!
The problem is that the passwords we use are not that mighty. In fact, we should just admit they’re actually LOUSY.
Putting “12345678” between you and a sophisticated cyber criminal is CRAZY, don’t you think?
So it’s time you admit your password sins and do something about them!
Here’s a simple question:
How many online accounts do you have?
If you work mostly online, you probably have over 100 (or 200 or more) accounts for all of the products and services you use. At some point, this gets very difficult to keep track of and even more challenging to keep them secure. The same goes for all your Internet-connected devices as well.
Below is all the information you need to set strong passwords and manage them securely in a single, easy-to-use guide.
We will go over all the best practices for online password security, from the do’s and dont’s to how to safely store your credentials. No fluff; just practical stuff you can apply to strengthen your passwords.
But first, let’s see why passwords are still critical for your online security.
How weak/default passwords can take down the Internet
Many have been claiming that “passwords are dead” for years now, but it turns out that no one has come up with a better alternative. So, for the foreseeable future, passwords will continue to be pivotal for your data protection.
Mundane as they may seem, these little strings of letters and (ideally) numbers and symbols are still the keys to the kingdom.
Unfortunately, many people still use terribly weak passwords and often reuse them. And many more just go on using the default ones they’re provided with.
The consequences are not pretty:
Over half of the confirmed data breaches that Verizon analyzed for their report “involved weak, default or stolen passwords”. This helped cyber attackers steal massive amounts of private data and use it for their financial benefit.
In the last months of 2016, flimsy or default passwords caused botnet malware to infect hundreds of thousands of Internet of Things devices, such as routers, security cameras, printers, digital video recorders, etc.
The Mirai botnet became notorious as it drew power from the compromised IoT gadgets to fuel huge DDoS attacks against Brian Kreb’s website, the French web host OVH and Dyn, an important DNS provider. This latter caused huge websites like GitHub, Twitter, Reddit, Netflix, Airbnb, eBay and others to become unreachable or experience connectivity issues.
Cybercriminals then used the same botnet to take Liberia’s entire Internet network offline, in a historic cyber attack. And then they used it again to take approximately 900.000 Telekom routers offline in Germany.
And remember this all started when attackers exploited default passwords on IoT devices:
Mirai is designed to leverage IoT by scanning the web for devices protected by factory-default passwords or hard-coded credentials, making them easy to compromise and infect. Once under the control of malicious actors, these devices are turned into a kind of massive botnet that can spam-DDoS websites and quickly shut them down.
You see, password security is no longer something nice-to-have. It’s essential not only to your own cyber security, but also to the entire Internet.
How would you feel if you were knocked offline by a cyber attack fueled by a massive botnet built by infecting gadgets left unprotected by their owners?
If you have your answer, let’s move forward and see how you can protect your accounts and devices from being used as toys in someone else’s game.
How secure is my password?
Here is a free tools you can use to get a real feel of how strong your average password is:
This password security checker will show you the difference between this:

And this:
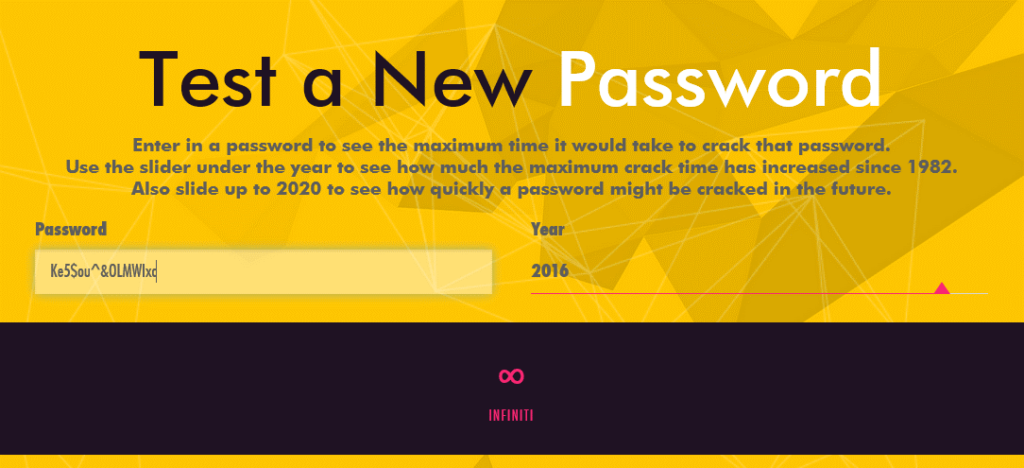
I think you’ll agree with me that “letmein” and “batman” are not suitable to protect your email or, worse, your bank account.
The thing about weak passwords is that cybercriminals have automated tools to crack them. What’s more, if they manage to get into your email account, they can use it to reset passwords for other accounts. If you’re using the same password for multiple accounts, then you’re just making things too easy for them.
Given that they’re tied together, all your accounts and/or devices will fall into their hands like domino pieces.
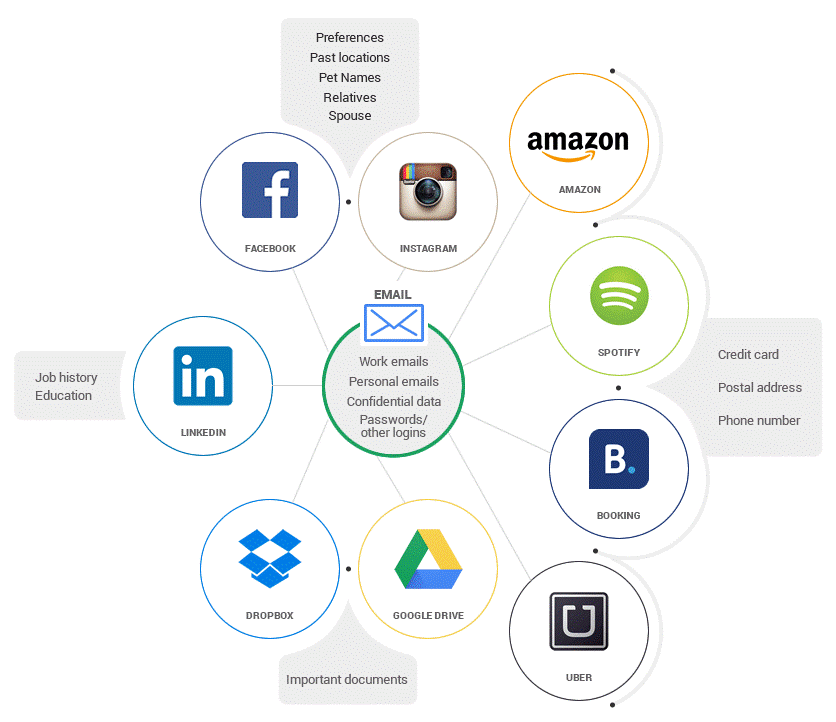
I know you can’t be scared into enhancing your password hygiene. The point here is to realize the importance and real-life impact of using proper passwords.
Now let’s see exactly how you can do it!
Password security tips: Dos & Don’ts
You probably think you already know all the rules for creating a good password. However, you might want to read some of the counterintuitive advice below. I think you’ll find the recommendations quite useful.
Don’t do this if you care about your online security
Don’t keep your passwords in text files, spreadsheets or other unprotected documents, all of which cybercriminals can easily steal, corrupt or delete.
Don’t save your passwords in browsers, because it’s not safe and most cyber attacks mainly target browsers as a way into the system.
Take a minute now to see if you have any stored in Chrome, Firefox, Internet Explorer, Safari and Microsoft Edge. If you do, delete them, but not before moving them to a password manager (keep reading for details).
Don’t use default passwords. They’re the first ones attackers try to unlock your accounts and devices with.
Don’t use notoriously weak passwords, like the ones on this list.
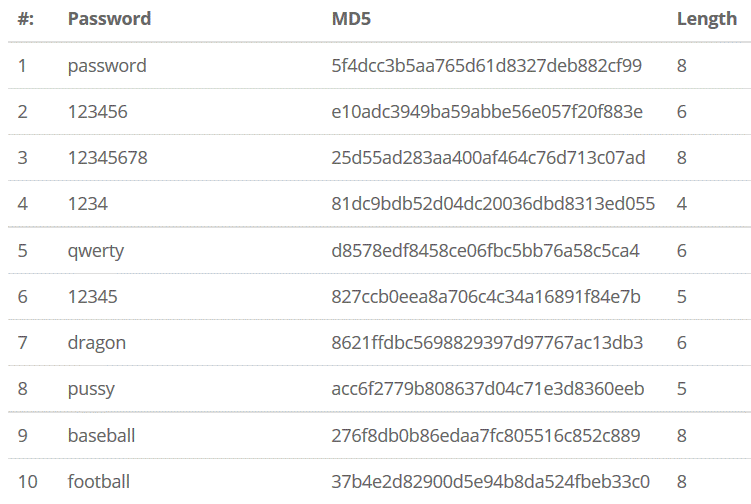
When creating new passwords, don’t use common phrases or words that you can find in a dictionary. There’s a type of attack that targets these specifically (more about it below).
Don’t create passwords that include your birth date or other information about you that people can easily find online.
Try to avoid using naughty words in your passwords. As cyber security expert David Harley says:
Passwords with a sexual connotation or using swearwords are very widely used, and therefore highly vulnerable to a guessing or dictionary attack.
Don’t use composition rules. If you have a habit of creating your passwords by using a recipe, such as “website name” + “year”, stop doing it. Once the tools the attackers use identify your recipe, cracking the rest of your passwords will be super easy to do.
Also, avoid password hints. There’s probably a ton of information about you online, so it won’t be too difficult to find out which high school you went to or the name of your pet. Predictability will give you away faster than you imagine.
Never use the same password for more than once account! This is an incredibly important rule to follow. In the words of Malwarebytes co-founder and CEO, Marcin Kleczynski:
I think that the biggest mistake that users make when it comes to their online assets is that they reuse passwords. They use the same password for their baking website as they do for their social profile, for example, and that creates the weakest link effect.
Don’t reset your passwords too often. This only works if you have strong passwords. If they’re long enough and complicated enough, there’s no need to change them frequently. The truth is that you might get lazy and start using shorter passwords again. But I have a solution for that just below, so stick with me.
Don’t share passwords in emails/instant messages/other platforms. If you share your passwords in plain text, people might see them by looking over your shoulder or they can find them while going through your inbox/IM history.
Never enter your passwords on someone else’s device. You don’t know if that system is safe and clean.
Now that you know what to avoid, let’s see how you can implement a better system to help you keep your passwords strong and unbreakable.
Remember: cybercriminals have ALL DAY long to crack your passwords. They also use advanced algorithms that can “try tens of millions of possible password combinations per second” (via Krebs on security). Are you sure you want to take your chances with those risks?
How to build robust and reliable passwords
A single, important step will help make password management simple and secure: using a password manager.
A password manager:
This is a software application that helps use securely store and organize your passwords. Passwords are kept encrypted, so you’ll have to create and use a master password to access your password vault. But the great part is that you will only have to remember a single password going forward, instead of hundreds.
Other features you’ll find in password managers include:
- Password generation;
- Form filing;
- Secure password sharing (you can choose if you want the other person to see the password or not);
- Convenient access from multiple devices (desktop, smartphone, tablet, etc.);
- Password audit, which will tell you how strong/weak your passwords are;
- Auto-change capabilities;
- Online shopping profiles, to store your card details and address, so you won’t have to put them in every single time you buy something online;
- Digital wallet to store all your payment method details, but also receipts and screenshots of your purchases;
- Fingerprint support, for those devices that have such an option;
- Offline access;
- Security breach alerts, if your email should be involved in a massive data breach and more.
If you still want to manage your password manually, here are the key tips to take into account:
Longer passwords are better. Make them over 10-15 characters long. The longer the password, the more time it takes to crack it.
Complexity is the goal! Include symbols, lowercase and uppercase letters and numbers. Scramble them like you scramble your eggs on Sunday morning.
Make them gibberish. Avoid predictable passwords, words that can be found in dictionaries (any language) and any type of reference, no matter how unfamiliar it may seem to you.
Keep your passwords unique. We’ve already talked about this one, but I can’t emphasize this enough: one account, one password.
Say NO to password sharing. Only you should know your passwords, no matter how much you trust your loved ones/friends/colleagues. Remember that you can share passwords safely through a password management app, and some apps even define levels of access (which are pretty common nowadays), so take full advantage of those options.
Test your password’s strength with the options I suggested at the beginning of the article.
Always enable two-factor authentication when given the option. We dedicated an entire security guide to 2FA, which I recommend you read and apply, for the sake of your data’s security.
Password security is one layer. Here are some critical others
Internet security is a matter of detail and one solution will never be able to cover all your protection needs. So here are some other key protection layers you should include among your safeguards:
- Backups are fundamental for your data’s safety, so if you’re a bit paranoid, you may want to keep your passwords by storing them in two separate password managers. That way, if something should happen to one of the solutions you use, you can always fall back to your plan B.
- Make sure that, when you log into an especially important account, the website has added protection through HTTPS. This is an indicator that the website uses a protocol for secure communication and that the data you send and receive through the website is encrypted. This protects you against cyber criminal attacks such as eavesdropping.
- If a website you’re visiting does not have HTTPS enabled, you’d better double check its safety and see if you’re sure you want to enter your credentials there. Additionally, you might not want to store your credit card details in that account either.
- Another key piece of advice is that your software updates are more important than you think. Every time you don’t have time to perform an update for one of your browsers or on a piece of software such as Java, Adobe Reader or Adobe Flash, a cybercriminal takes advantage of a flaw left uncorrected. Updates are not only used to deliver better functionality, but security patches as well.
When left outdated, your software exposes you to serious cyber attacks, such as Zero Day attacks, which are downright vicious. Automating software updates can save you a ton of time and trouble, and it can be accomplished easily with a product like Premium Home Security.
- Don’t compromise yourself. Sometimes, human error is the biggest liability in our data’s security, so try to keep paying attention to how you share passwords. When you’re either delegating work, go for a vacation or a sick leave, give access to business partners, or even when a colleague asks you for a passwords, chose the safe way to do it.
- And also be aware of the people around you. Someone might just look over your shoulder (shoulder surfing attack) and check out your password. The shorter and the weaker, the easier it will be to remember it. Be mindful of your surroundings, both when you’re online and offline.
How cybercriminals try to break your passwords
If you’re wondering how Internet criminals go about cracking your credentials, here’s the shortlist:
Phishing is a method that cyber criminals use to sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by posing as a trustworthy entity in emails or other means of electronic communication.
So if you ever receive an email that looks like this:
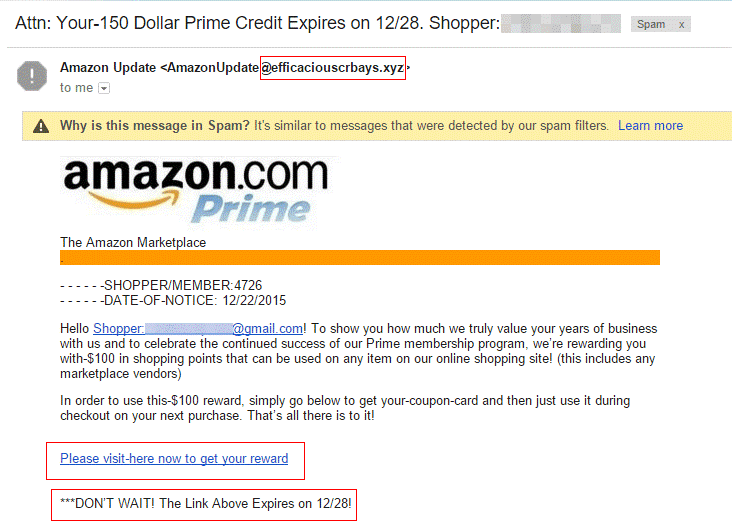
DON’T CLICK ON IT! Mark it as spam and make sure you never click on the links inside it.
Brute-force attacks are a tactic used by cybercriminals to find out what your passwords are. They systematically check all possible keys or passwords until they find the right one. For this, they use algorithms that can try all of these combinations superfast. Your short, repetitive passwords are no match for them!
Dictionary attack – you’ve read about this one already, but let’s go over how it happens. By using an algorithm, the attacker tries hundreds of combinations derived from lists of words in dictionaries.
Password sniffing is another way of collecting your confidential credentials on unencrypted websites. Because the data that flows to and from the website is unsecured, an attacker can easily pick it up by using the right tools for the malicious job.
Keylogging (also called keystroke logging) is a method that cyber criminals use to record (or log) the keys struck on a keyboard in order to acquire confidential information about the user. This is usually done in a concealed manner, so that the person using the keyboard won’t know that their actions are being monitored. So if you’re typing your online banking account password into your computer, and there’s a keylogger installed in your system, the cybercriminals behind this attack will easily retrieve your credentials.
Social engineering is one of the most commonly used methods of cyber hacking, which requires little to know technology and relies on psychological manipulation. The victim is persuaded to perform certain actions or divulge confidential information, among which are usually passwords to confidential data.
Shoulder surfing is another type of attack I’ve mentioned before. This involved someone simply glancing over your shoulder to see what you’re typing. Weak passwords can get you in big trouble in this case too.
Database hacking – if a cybercriminal gains access to a company’s user database that contains the credentials of thousands or millions of customers, and you’re among one of those customers, then you could be exposed as well. Hundreds of data breaches have made the headlines in 2020, and they just seem to keep on coming.
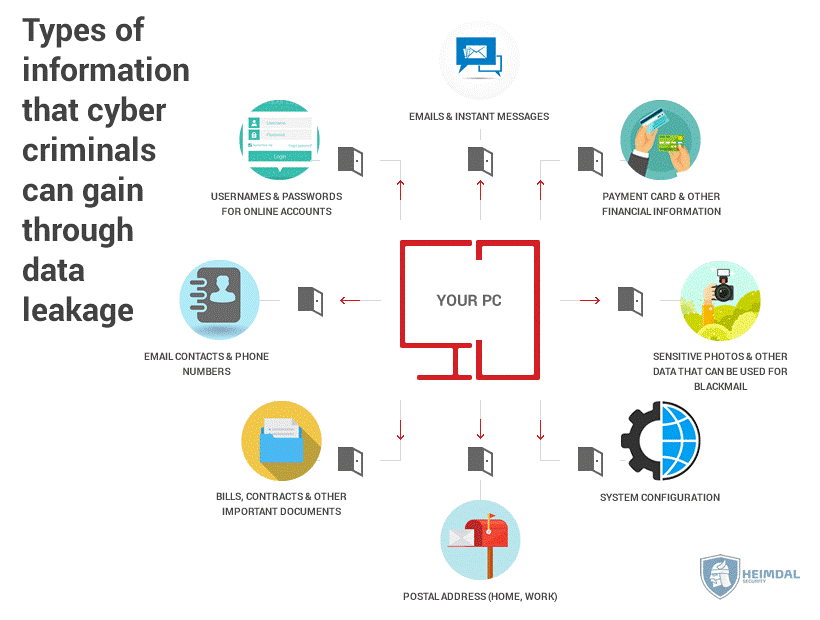
Of course, attacks using malware, such as man-in-the-middle attacks, malvertising, spyware, adware, etc., or different types of malicious software can also endanger your passwords, as most cyber-attacks also have a component that aims to capture your credentials.
Alternatives to passwords for authentication
For the moment, no other authentication system proved capable of replacing passwords. None of the options on the market managed to be as secure, usable and scalable as passwords are, but that doesn’t mean they can’t become all these things in the future.
Alternative authentication mechanisms include:
- Time-dependent passwords, which expire or change after a defined amount of time;
- Single-use passwords, which can only be used once, as the name already indicates. You’re probably already using these for your online banking system, where they’re called Transaction Authentication Numbers;
- Public-key cryptography is another option that’s well explained in this guide any Internet user can understand;
- Biometric authentication that relies on personal characteristics that cannot be changed, such as your fingerprint, your retina or other personal details (this list is quite comprehensive).
- Passwords based on something else rather than text, such as pictures, colors, graphics and other elements.
The list could go on, but I’m sure that, by now, you already have a pretty accurate picture of the situation.
Conclusion
Passwords will be around for a while, that’s for sure. Before we start using biometric technology or a groundbreaking innovation comes into play, we will still rely of this method of authentication.
To end things on a funny, but educative note, here’s Edward Snowden talking about password security with John Oliver. It’s a 3 minute video that could, perhaps, talk you into making some changes, if I haven’t managed to persuade you until this point.
This course is presented in partnership with Heimdal Security – a worldwide leader in enterprise and consumer cyber security solutions.



