In the previous lesson we talked about increasing online safety by adjusting your browser’s security settings, but do you know how to protect your valuable data on public Wi-Fi networks that are anything but safe?
And how exactly do you increase security on your own home Wi-Fi network?
Before we follow the steps that should be taken to increase protection for a home wireless network, We would like to give you some valuable insights on how to defend your privacy on public wireless networks.
So it is okay to use public WI-Fi to buy stuff online, check online banking accounts or enter passwords to crucial websites?
The answer is simple: NO.
Malicious hackers might use Wi-Fi sniffers and other methods to intercept almost all the data that goes through the router, such as emails, passwords, addresses, browsing history and even credit card data.
You can minimize these Wi-Fi dangers by using only routers encrypted with WPA2.
Here are some examples of public Wi-Fi attacks to get a better picture of what you’re going up against.
- Brute-force/cracking attacks: These can be used by malicious hackers to bypass a public Wi-Fi password either by mass testing a huge amount of passwords (brute force attacks) or by using specialized software and tools to trick the router into revealing the password (cracking attack).
- War driving: This involves the malicious hacker driving around various locations, looking for vulnerable Wi-Fi connections he can later exploit.
- Wi-Fi sniffing: This process involves intercepting specialized tools or software than can intercept and reassemble internet data sent between a router and a device. From a technical perspective, it’s very easy to set up a Wi-Fi sniffer since all you need is a laptop and some widely available software to add the necessary functions.
- Karma Attacks. If you’ve seen Mr. Robot, then you’re probably familiar with this type of attack. To carry this one out, a malicious hacker needs a specialized hardware tool which can create a clone of the target Wi-Fi, tricking connected devices into switching to the cloned network. At this point, the malicious hacker has complete visibility over everything the connected devices are doing while hooked up to the network.
In one of the more thought provoking cybersecurity news that we’ve come across, a cybersecurity researcher managed to completely take control of a city-wide public Wi-Fi.
Every once in a while however, you’ll probably need to connect to a public WiFi network. But you can mitigate some of the risks involved by following a few basic both your device and data.
1. Turn off public network sharing when connected to an unsecured Wi-Fi.
It’s usually fine to allow resource sharing, such as connected printers or public folders, if you device is hooked up to either your home or work network. However, an open Wi-Fi poses a security risk.
For instance, a malicious hacker might get access to important files and documents stored on the cloud, or they might even do a reverse hack, where they break into a printer first and then to any other connected devices.
To turn off public sharing, follow these steps:
1. Go to your Windows Control Panel.
2. Access the Network and Sharing Center window.
3. Click Change Advanced Sharing Settings.
4. Select the Public profile.
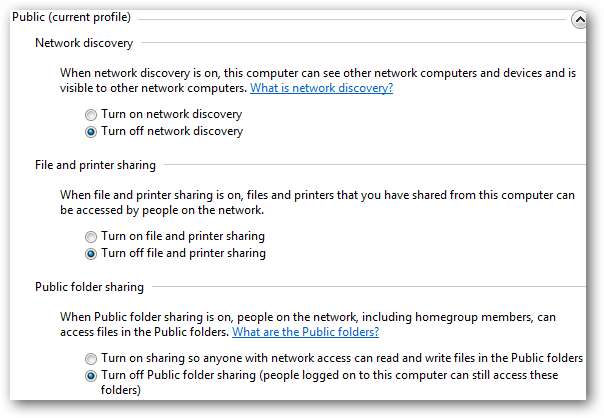
5. Turn off File Sharing, Network Discovery, and Public Folder Sharing, in case they aren’t already OFF. Usually, by simply choosing that you are connecting on a Public network, these options are automatically turned off.
(The steps may differ on different Windows operating systems.)
2. Keep the Firewall Enabled
Keep your Windows firewall enabled at all times. If you have a security product with an even better firewall, then use that one instead.
Usually we turn off the Windows firewall because of the annoying popups and notifications and then just completely forget about it. If you want to restart it, then head over to the Control Panel, go to System and Security and select Windows Firewall.
(The steps may differ on different Windows operating systems.)
3. Use secure websites for sensitive operations
First of all, we don’t recommend running any important operation or financial transaction on an open Wi-Fi because of the security risk involved. This being said, if you still need to use a public network to check your bank balance, make sure you visit a secure website, or go one step further and use specialized secure browsers.
To know you’re using a secure site, look to the left of the web address and find the “Lock” icon. This indicates you are on an encrypted or verified location.
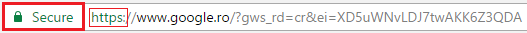
At the same time, check the web address starts with “https://“. The “S” is from “secure socket layer” and you know you are going to a site where communication is encrypted.
If you don’t want checking all the time the web address, use HTTPS Everywhere, which is available for Firefox, Chrome, and Opera. This little extension has the role to encrypt your communications with many major websites, making your browsing more secure and safe from online criminals.
Even if you don’t use this extension, many sites like Facebook or Gmail use https automatically.
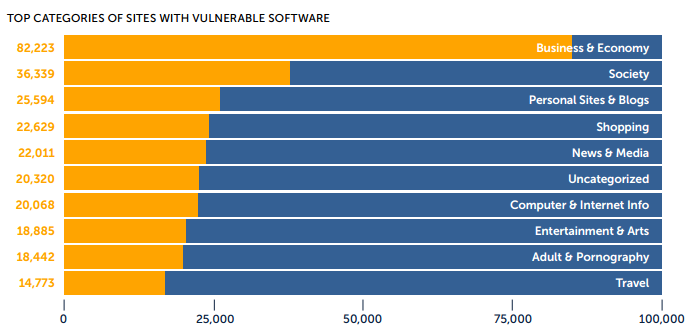
In a surprising twist, some of the most insecure websites out there are the ones centered on “serious topics” such as business & economy sites. And in an even more surprising twist, porn sites tend to be more secure than news sites.
4. Use a Virtual Private Network
Public networks are favorite places for cyber-criminals to retrieve sensitive data by using wireless sniffers in order to obtain emails, passwords and other such data sent over the unsecured Wi-Fi network.
A quick way to stay more secure is to use a “private browsing” session, which disables the browser to remember your browsing history and storing data in the cache. While this stops a malicious hacker from accessing past data, it can’t prevent him from listening in to your browsing session in real time.
That’s why we recommend you use a VPN when setting up a connection to an unsecured public Wi-Fi.
A VPN, short for Virtual Private Network, hides your IP address by encrypting your connection and allowing you to browse online in anonymity. In most cases, not even your ISP is able to track what exactly you are up to while online.
Using this method you protect your online privacy and you keep your valuable information from cyber threats, online scams, identity breaches or phishing attempts.
To keep your online session private on public wireless networks, we recommend a popular VPN solution like CyberGhost. If CyberGhost isn’t to your taste, then here’s a complete ranking of the best VPN solutions out there.
5. Turn the Wi-Fi connection OFF
Are you done using the Wi-Fi network? Then don’t forget to turn it off.
There is no reason to stay connected more than you need. The longer you’re on the network, the more you expose yourself to the dangers of public Wi-Fi such as sniffing or malicious software. It’s also bad for your battery life.
6. Update and patch everything
Keep your Windows operating system up-to-date
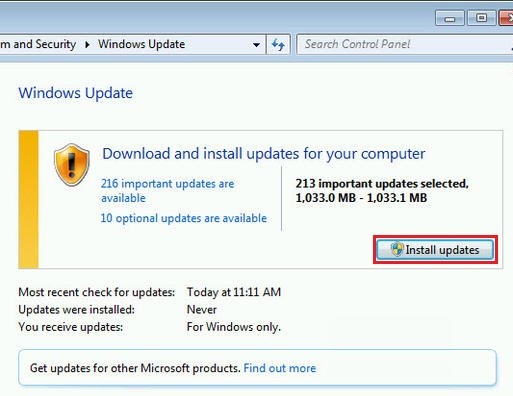
Updates are important for your cybersecurity since they patch a lot potential vulnerabilities in your operating system or other programs.
To make your Windows OS update automatically, follow these steps:
1. Go to your Windows Control Panel window.
2. Select Windows Update and click Change settings.
3. Make sure Install updates automatically is selected.
Software vulnerabilities in third-party programs such as Flash or Chrome also pose a security risk by tricking the software into downloading and running malicious software.
Unfortunately, not all third-party software programs have an automatic update function, so chances are you will have to do the updates manually, which is a huge chore and time waste.
It’s for this reason that we propose you use Heimdal Premium Security Home, which can automatically update without bothering you with popups and annoying notifications.
7. Don’t connect to a public Wi-Fi without a reliable antivirus
Not all antivirus programs are created equal. A good one can make all the difference when it comes to keeping your computer free of malware.
Three things are important when choosing a good antivirus: virus scanners, heuristic analysis capabilities (meaning, how well an antivirus can detect unknown malware) and how frequently is it updated with the latest malware definitions and other software patches.
8. Don’t browse without a good anti-spyware solution
First, what do we mean by spyware?
Spyware is a type of malware used to intercept internet data and do many other nasty things to your computer. Here are just some of the symptoms:
- pop-up windows spring up everywhere
- strange error messages
- web browser search engine has been replaced with something fishy
- web browser home page is not the one you set
- unknown toolbars appear in your browser
- frequent system slowdowns.
How do I protect from spyware?
Spyware can infect you at any time, but the lax security on public Wi-Fi increases the likelihood of catching the bug.
You can however use some specialized software such as Malwarebytes or Lavasoft’s Ad-Aware which are specialized around finding and removing spyware and other similar threats.
In the end however, the best anti-malware solution out there are your own Internet skills. That’s why we always recommend you:
- don’t click suspicious fishing links or random pop-up windows.
- don’t reply to strange questions in your web browser or your e-mail inbox.
- be diligent and careful in the applications and software you download.
9. Don’t run financial transactions without special protection
We’ve talked about this earlier but this deserves a section all of its own.
Doing financial transactions over an unsecured public Wi-Fi is risky business.
Nevertheless, if you really need to access your bank account or pay online, we recommend you use a special security solution that can scan incoming and outgoing internet traffic for malicious software before these can infect your device and allow cybercriminals to hack you.
This software represents a complementary layer of security for the traditional antivirus solutions and it’s just one way you can strengthen your financial security.
10. Secure your browser before you go online
Browsers are main gateway for Internet traffic, and because of this, it is the first target of many malware programs. That’s why a safe and secure browser will filter out many potential threats and minimize some of the risks associated with the Internet.
Here are just a few of the steps you can follow to make sure your browser can cope:
- Make sure you have the latest browser version and security patches.
- Access and modify your browser’s security settings.
- Use private browsing sessions to minimize how much data a cybercriminal can gather from you. To step up your privacy and anonymity use a proxy or a VPN such as CyberGhost.
11. Use two-factor authentication everywhere
This option is an extra security step you need to complete in order to login into your account. Use this whenever possible, especially when it comes to your Facebook and email accounts.
This extra security step requires you type in a security code you received on your phone before you log in. This way, a malicious hacker can’t log in without also having access to your phone number or SMS inbox, even if they know your email account and its associated password.
Here’s a more in-depth guide on how two-factor authentication works and how you can set it up for your email and social media accounts.
Conclusion
It’s not really feasible to always avoid public Wi-Fi and use your data plan, especially if you don’t have much data left, or if you happen to visit another country. However, awareness of the risks involved will go a long way in helping you stay clear of most dangers.
That’s it for today! Thank you for sticking with us. In our next lesson we’ll go over how to keep your email accounts safe and secure from malicious hackers and other threats, all by doing just a few easy steps!
This course is presented in partnership with Heimdal Security – a worldwide leader in enterprise and consumer cyber security solutions.



